Our cinema cameras are exposed to hackers. A recent cybersecurity study conducted by leading IT security company has revealed major breaches in the Picture Transfer Protocol of modern cameras when connected to WiFi. Your precious media might be vulnerable to hackers and malware. Read below how to avoid it.

Picture Transfer Protocol (PTP): A simple pathway to hack your camera
Check Point, a leading provider of cybersecurity solutions, revealed that via connections to WiFi networks, modern cameras are vulnerable to ransomware and malware attacks.
Since modern cameras no longer use film to capture and reproduce images, the International Imaging Industry Association devised a standardized protocol known as Picture Transfer Protocol (PTP) to transfer digital footage from the camera to PC. Initially focused on image transfer, this protocol has evolved to include dozens of different commands that support anything from taking a live picture to upgrading the camera’s firmware.
Cameras are no longer just connected to the USB, but the WiFi network and its surrounding environment. That makes them more vulnerable to threats as attackers can inject ransomware into both the camera and PC. The footage could end up being held hostage until the user pays the ransom for them to be released
Eyal Itkin, Security Researcher, Check Point Software Technologie
Canon EOS 80D as a reference
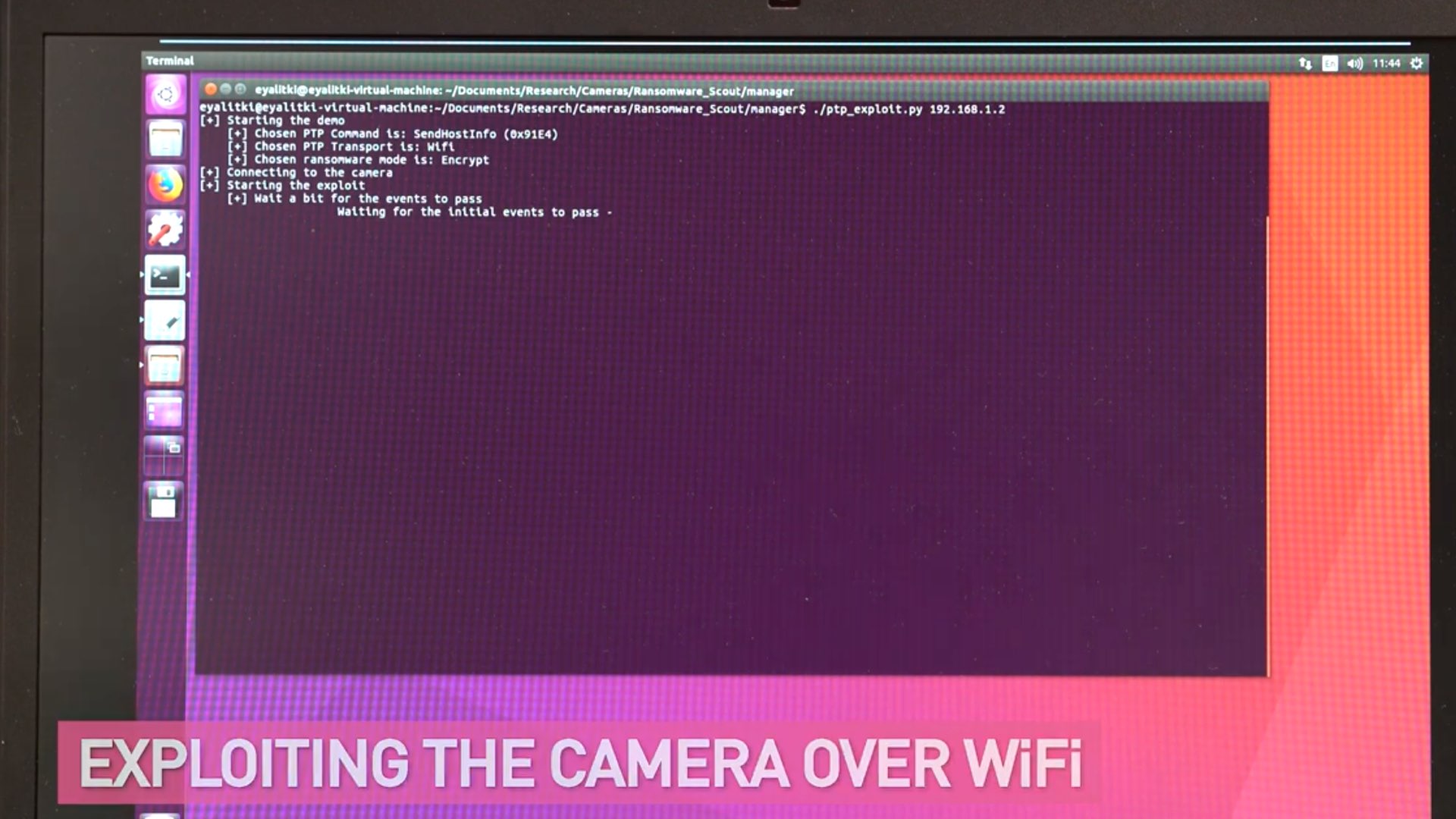
For the research, Check Point used Canon’s EOS 80D DSLR camera which supports both USB and WiFi, and critical vulnerabilities in the PTP were found. Given that the protocol is standardized and embedded in other camera brands, Check Point believes similar vulnerabilities can be found in cameras from other vendors as well. “Any ‘smart’ device, including the DSLR camera, is susceptible to attacks,” says Eyal Itkin, Security Researcher, Check Point Software Technologies. “Cameras are no longer just connected to the USB, but the WiFi network and its surrounding environment. That makes them more vulnerable to threats as attackers can inject ransomware into both the camera and PC. The footage could end up being held hostage until the user pays the ransom for them to be released.”
FYI: PTP as an ideal layer for hackers
From an attacker’s perspective, the PTP layer looks like a high target:
- PTP is an unauthenticated protocol that supports dozens of different complex commands. Vulnerability in PTP can be equally exploited over USB and WiFi.
The WiFi support makes our cameras more accessible to nearby attackers. - WiFi – An attacker can place a rogue WiFi access point at a tourist attraction, to infect your camera.
- Hacking and penetrating the PTP protocol with the help of Magic Lantern documentation (in the case of Canon EOS).

Magic Lantern (ML) is an open-source, free software add-on that adds new features to the Canon EOS cameras. As a result, the ML community already studied parts of the firmware and documented some of its APIs. Attackers are profit-maximizers. They strive to get the maximum impact (profit) with minimal effort (cost). In this case, research on Canon cameras will have the highest impact for users and will be the easiest to start, thanks to the existing documentation created by the ML community.

Furthermore, it’s important to note, that one of attacker’s first step is to check if there is a publicly available firmware update file in the vendor’s website. That’s easy because almost any cinema manufacturer uploads firmware updates to its website. In most cases, those firmware updates are encrypted/compressed. However, hackers will finally manage to decrypt the firmware using dedicated tools. In the fact of Canon EOS 80D, ML (Magic Lantern) documentation was more than helpful (for the bad guys).
Go here to read more about the methods and process of this case study.
The hack of the D80 is demonstrated in the video below:
A filmmaker’s nightmare
The attacker, nearby (WiFi), can also propagate to and infect your beloved cameras with malware. Imagine your RED get hacked by using a Wi-Fi network. In that case, all your media stored in Mini-Mag will be encrypted, which means you can’t access it, only by paying ransom to attackers.

Canon’s response
Check Point Research informed Canon about the vulnerabilities, and the companies worked together to patch them.
Here is Canon’s response to the successful attempt of hacking the D80: “An international team of security researchers has drawn our attention to a vulnerability related to communications via the Picture Transfer Protocol (PTP), which is used by Canon digital cameras, as well as a vulnerability related to firmware updates. Due to these vulnerabilities, the potential exists for a third-party attack on the camera if the camera is connected to a PC or mobile device that has been hijacked through an unsecured network. At this point, there have been no confirmed cases of these vulnerabilities being exploited to cause harm, but in order to ensure that our customers can use our products securely, we would like to inform you of the following workarounds for this issue“.
- Ensure the suitability of security-related settings of the devices connected to the camera, such as the PC, mobile device, and router being used.
- Do not connect the camera to a PC or mobile device that is being used in an unsecured network, such as in a free Wi-Fi environment.
- Do not connect the camera to a PC or mobile device that is potentially exposed to virus infections.
- Disable the camera’s network functions when they are not being used.
- Download the official firmware from Canon’s website when performing a camera firmware update.
Conclusions
The PTP protocol is standardized and embedded in other camera brands, which means that almost every cinema camera which uses this protocol is exposed for malware. In that case, the media can be encrypted, and filmmakers will not be able to access their media. To avoid it:
- Make sure your camera is using the latest firmware version.
- Turn off the camera’s WiFi when not in use.
- When using WiFi, prefer using the camera as the WiFi access point, rather than connecting your camera to a public WiFi network.
This safety measures will reduce the chances of your camera being hacked. Furthermore, PTP is not the sole pathway of hacking your camera.